#
Exploring Vulnerabilities: A Hands-On Assessment with OpenVAS(GVM)#

Introduction
In today’s ever-evolving cybersecurity landscape, identifying and mitigating vulnerabilities is a vital practice. In this case study, I explore the vulnerability assessment of CyberTech Solutions’ network using OpenVAS on Kali Linux. By conducting a comprehensive scan, analyzing results, and recommending remediations, this exercise demonstrates the importance of proactive measures in securing IT infrastructure.
Setup and Installation
To carry out this assessment, I installed and configured OpenVAS on a Kali Linux system. OpenVAS, a powerful open-source vulnerability scanner, allows for detailed analysis of network security.
Steps to Install OpenVAS:
- Install OpenVAS:
sudo apt update && sudo apt install -y openvas
- Set up OpenVAS:
sudo gvm-setup
- Start the service:
sudo gvm-start
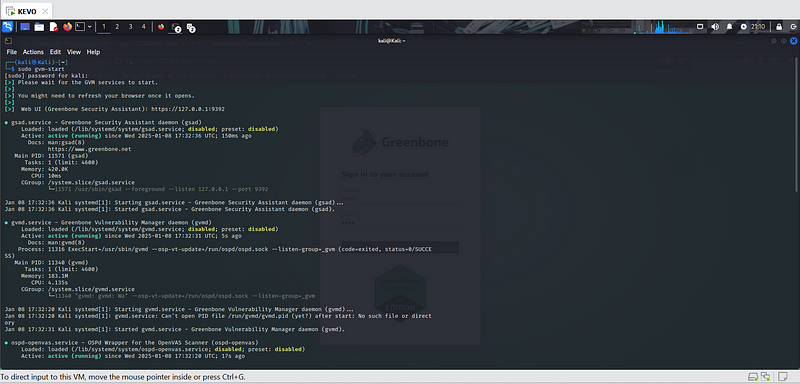
- Access the Web Interface: Navigate to https://<your-ip>:9392 and log in using the credentials set during the setup.
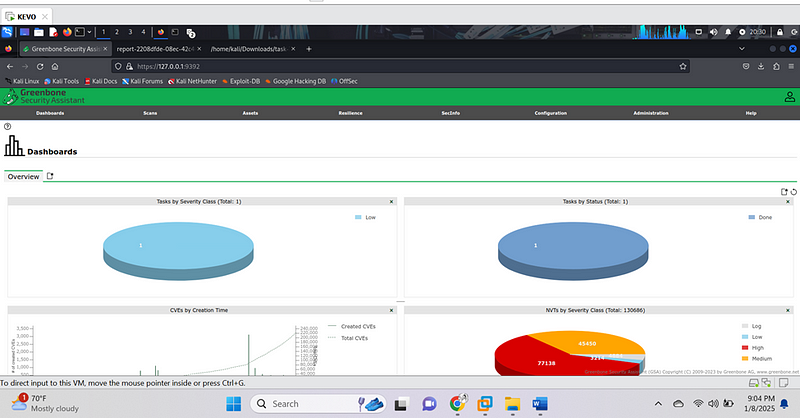
These steps ensure a ready-to-use environment for scanning. For an enhanced experience, screenshots of the installation process are included.
Scanning Process
Once OpenVAS was configured, I created a scanning task to assess CyberTech Solutions’ network, targeting the IP address 10.6.6.12. The steps included:
- Configuring the Target:
- Added 10.6.6.12 as a new target under Configuration > Targets.
- Selected “Full and Fast” as the scan configuration for efficiency and coverage.
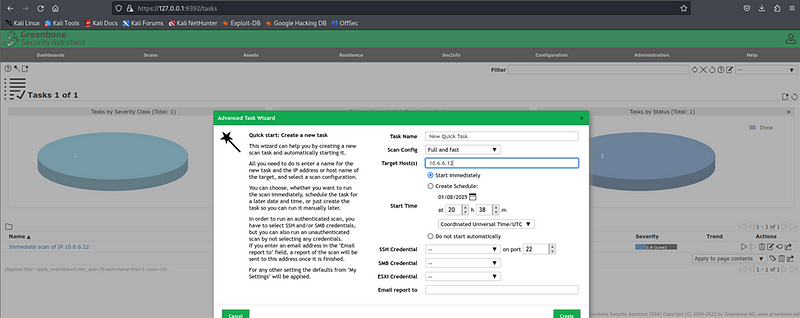
2. Running the Scan:
Created a new task under Scans > Tasks, linked it to the target, and started the scan.
Monitored the progress and reviewed results upon completion.
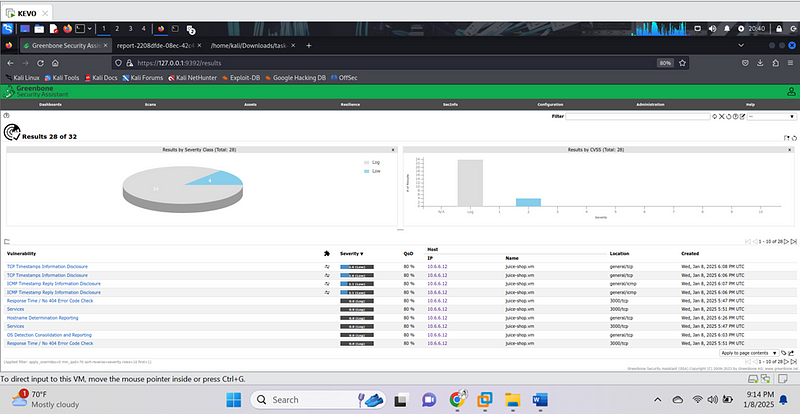
Findings
The scan yielded two low-severity vulnerabilities. Here are the details:

Detailed Analysis
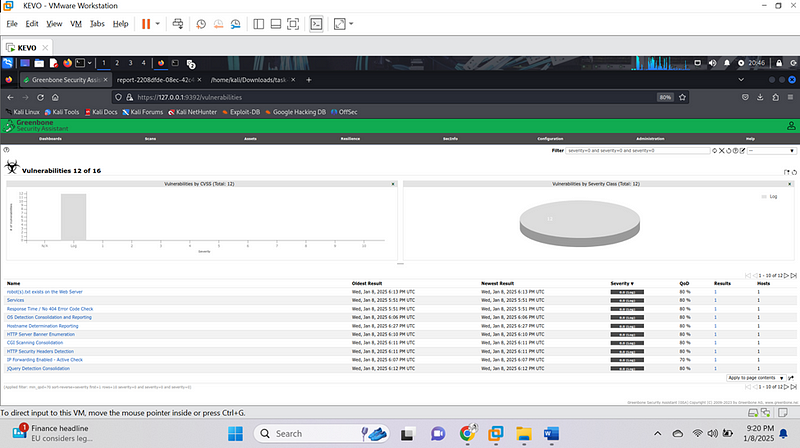
- TCP Timestamps Information Disclosure
- Impact: The remote host implements TCP timestamps, which can disclose uptime information.
- Mitigation: Add the following to /etc/sysctl.conf and apply it:net.ipv4.tcp_timestamps = 0sudo sysctl -p
- ICMP Timestamp Reply Information Disclosure
- Impact: ICMP timestamp replies could be exploited in timing attacks.
- Mitigation: Configure the firewall to block ICMP packets from untrusted networks.
Analysis and Prioritization
Although both vulnerabilities were rated low, they could be leveraged in larger attacks. Prioritizing these issues ensures a stronger security posture:
- Disable TCP timestamps to reduce information leakage.
- Restrict ICMP packets using firewalls for an additional layer of defense.
Conclusion
This vulnerability assessment highlights the value of tools like OpenVAS in identifying and mitigating risks. Regular scans and proactive remediation are essential to maintaining a secure network. By addressing even low-severity issues, organizations can reduce their attack surface and improve resilience against potential threats. ::: ::: ::: :::
By Kiplagatkelvin{.p-author .h-card} on January 8, 2025.
Canonical link{.p-canonical}
Exported from Medium on February 13, 2025.
