CyberTech Solutions Network Segmentation Plan for IoT and SCADA Devices#

1. Introduction
As IoT and SCADA devices become increasingly integral to modern businesses, they also introduce significant security risks. CyberTech Solutions must address the potential vulnerabilities posed by these devices. This network segmentation plan aims to mitigate the risk of IoT and SCADA devices being compromised and protect critical business systems by implementing a secure and isolated network architecture.
2. Assessment of IoT and SCADA Risks
CyberTech Solutions utilizes IoT and SCADA devices for operational efficiency and real-time data processing. However, these devices can be vulnerable to several risks, such as:
- Unpatched firmware: Leaving devices exposed to known vulnerabilities.
- Insecure communication protocols: Use of non-encrypted or easily intercepted communication channels.
- Weak authentication: Many IoT and SCADA devices rely on default credentials or have inadequate authentication mechanisms.]{#4e73}
- Lack of network isolation: IoT and SCADA devices are often on the same network as critical business systems, increasing the risk of lateral attacks.
If compromised, these vulnerabilities could lead to unauthorized control of SCADA systems, operational disruption, data theft, or malware spread across critical business networks.
3. Proposed Network Segmentation Plan
To address these risks, we propose the following network architecture that isolates IoT and SCADA devices from the core business network. The segmentation will help ensure that if IoT or SCADA systems are compromised, attackers cannot gain access to sensitive business systems.
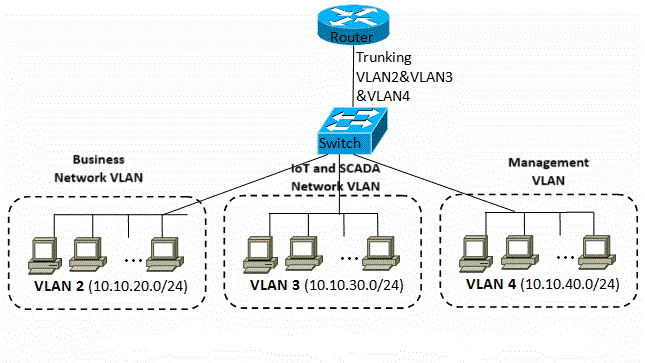
3.1 VLAN Architecture
We recommend segregating IoT and SCADA devices into their own Virtual Local Area Networks (VLANs). Each VLAN will be dedicated to specific device groups:
- VLAN 1: IoT devices
- VLAN 2: SCADA devices
- VLAN 3: Critical business systems
The VLAN architecture will ensure that devices on different networks cannot communicate directly with one another, thus limiting the potential spread of malware or attacks.
3.2 Firewalls and Access Controls
To further isolate these networks, we will implement firewall rules that control and restrict traffic between the VLANs:
- Internal Segmentation Firewall (ISFW): This firewall will be positioned between the IoT, SCADA, and business system VLANs. It will block all unnecessary communication, only allowing specific traffic such as device updates, monitoring data, or authorized user access.
- Access Control Lists (ACLs): These ACLs will be configured to ensure that only authorized devices and users can access the IoT and SCADA VLANs. Furthermore, only essential services and protocols, such as HTTPS for device communication, will be allowed between VLANs.
3.3 Network Access Control (NAC)
NAC solutions will be deployed to prevent unauthorized devices from connecting to the IoT or SCADA VLANs. All devices will be subject to authentication and posture assessment, ensuring only compliant devices are permitted to connect.
3.4 Role-Based Access Control (RBAC)
To minimize insider threats, RBAC will be implemented to control user access. Only authorized personnel with specific roles will have access to IoT or SCADA systems. The RBAC policy will also enforce the principle of least privilege.
4. Traffic Control and Monitoring
Monitoring and controlling network traffic is crucial to maintaining security. The following strategies will be employed to manage traffic flow between VLANs and detect any potential threats:
- Intrusion Detection and Prevention Systems (IDS/IPS): IDS/IPS solutions will be deployed within the IoT and SCADA VLANs to detect any suspicious traffic or attempted breaches. These systems will alert security personnel to any anomalous activity.
- Logging and Auditing: Firewalls, switches, and other network devices will log all traffic between VLANs. These logs will be analyzed to detect patterns indicative of security issues.
- Regular Network Audits: Periodic network security audits will be conducted to ensure that segmentation and access controls are functioning as intended.
The diagram below shows the real configuration setup of the IOT/SCADA
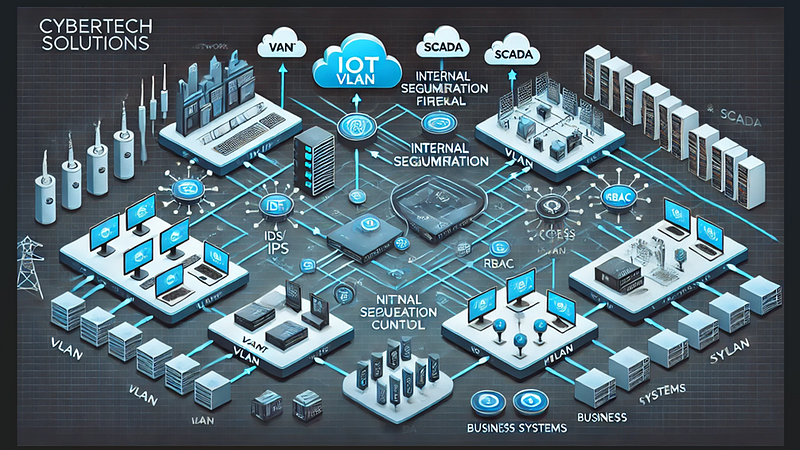
5. Conclusion
By isolating IoT and SCADA devices in dedicated VLANs, restricting their communication with critical business systems using firewalls, and employing robust monitoring and control measures, CyberTech Solutions can significantly reduce the risk of attacks originating from compromised IoT or SCADA devices. This network segmentation plan provides a comprehensive strategy to secure CyberTech’s network infrastructure and safeguard its operations.
By Kiplagatkelvin{.p-author .h-card} on October 21, 2024.
Canonical link{.p-canonical}
Exported from Medium on February 13, 2025.
